Vulnerability Management with DefectDojo
Last Friday, I had the pleasure of speaking at the Hackerkiste Conference in my hometown Augsburg 🥨 — about one of my favorite topics:
How to make Vulnerability Management actually work in modern DevSecOps environments. Here’s a small blogpost about it.

Imagine it’s Friday afternoon.
A critical vulnerability is disclosed in a widely used library — one that your applications also depend on.
When your developers return on Monday morning, a pull request with the fix is already open, all tests are green, and the ticket just needs to be merged and deployed.
That’s what modern DevSecOps should look like: automated detection, prioritization, and remediation — before attackers can exploit the weakness.
Why Vulnerability Management?
Security today is not just about reacting to hacks — it’s about staying ahead.
Besides regulatory pressure (e.g. NIS2, CRA, ISO 27001), continuous attacks and new vulnerabilities make it essential to monitor your entire software supply chain.
The challenge: there are countless scanners — SAST, SCA, DAST, container, IaC, WTF — each producing different formats, priorities, and reports.
This leads to scanner overload and fragmented visibility.
That’s why we need Vulnerability Management: to consolidate, track, and prioritize findings efficiently.
OWASP and DefectDojo
The Open Web Application Security Project (OWASP) provides an open-source solution for Application Security Posture Management: OWASP DefectDojo.
It aggregates findings from multiple scanners, deduplicates results, provides dashboards, and integrates directly with tools like Jira.
There’s a demo available at https://demo.defectdojo.org/. Log in with admin / 1Defectdojo@demo#appsec.
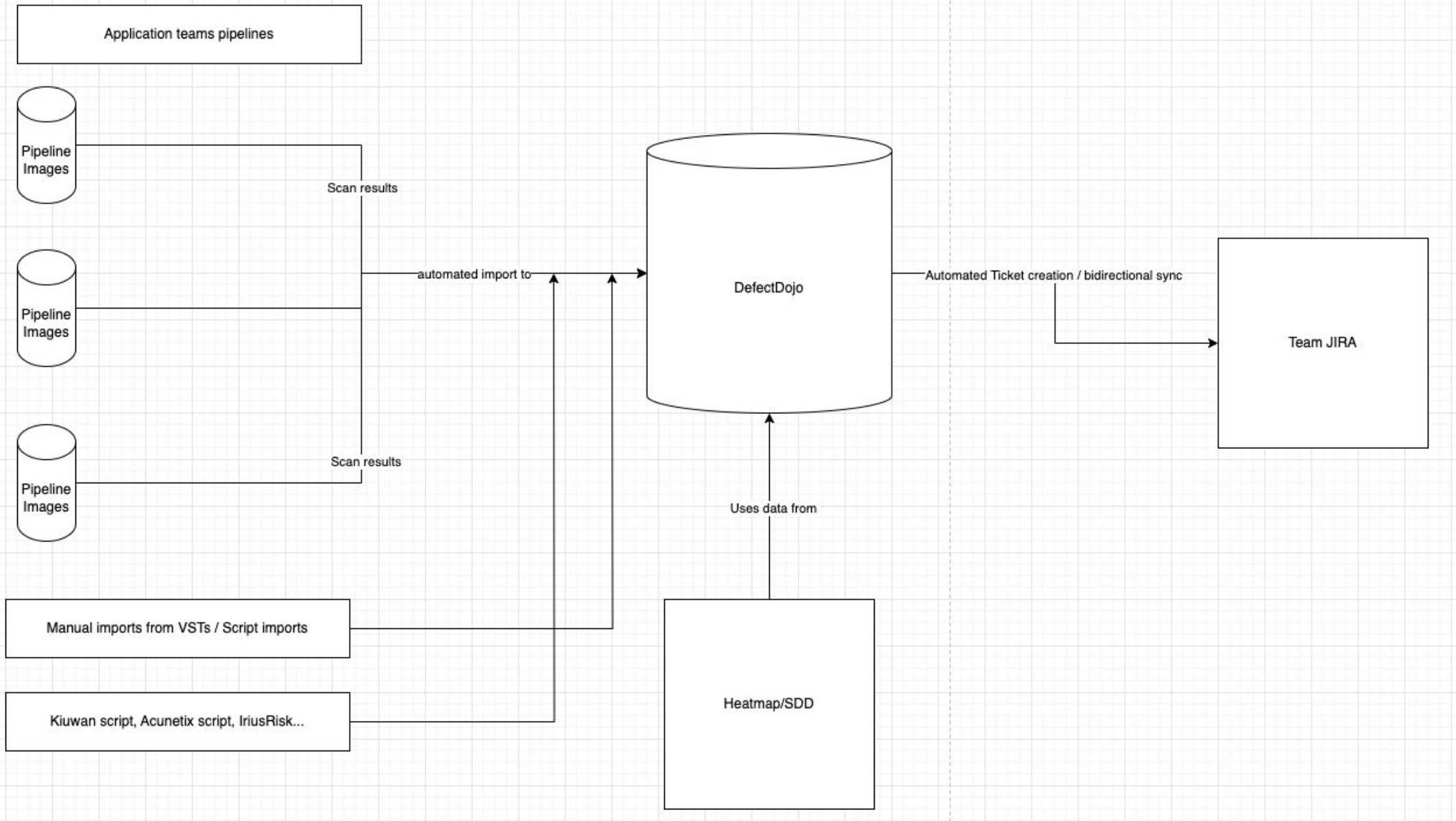
The Architecture
Our architecture for automated vulnerability management consists of three main components:
1️⃣ GitLab (left)
GitLab CI/CD pipelines execute all relevant security scans using custom container images.
Each image includes a bit of Python logic that automatically uploads results from the application pipelines directly to DefectDojo.
This ensures that every security scan from every team ends up in one central place.
2️⃣ DefectDojo (center)
At the heart of the system, DefectDojo acts as the central Application Security Posture Management platform.
It normalizes and deduplicates scanner data, tracks remediation progress, and provides management-level dashboards and reporting — critical for compliance and executive visibility.
3️⃣ Jira (right)
Between DefectDojo and Jira sits a thin Python integration layer.
It automatically creates and updates tickets in Jira for verified findings, linking them to the right teams and repositories.
This closes the loop between detection and remediation.
Challenges We Faced
To be very honest here, there were some challenges:
- DefectDojo maintenance required ongoing updates and tuning, e.g. the database migration from MySQL to PostgreSQL was a major effort.
- JIRA Spam: False positives had to be filtered before creating Jira tickets.
- And overall, ensuring smooth integration across tools required constant attention.
A Practical Alternative
If you don’t want to build such an automation framework from scratch, a practical alternative is to explore GitLab’s integrated security features - where you get everything from this architecture (and more) out of the box. This can drastically reduce complexity and maintenance overhead.
Get in Touch
If you’re interested in setting up a similar vulnerability management process or improving your DevSecOps workflows:
📧 Reach out to me or the team at secureIO GmbH — we’d love to help.
You can download my slides from the presentation here:
Download Slides (PDF)
Questions, Comments, Notes? Send me an email.